Threat Watch
Instantly assess your cyber security health with Threat Watch and gain actionable insights to protect your digital wo...
Visit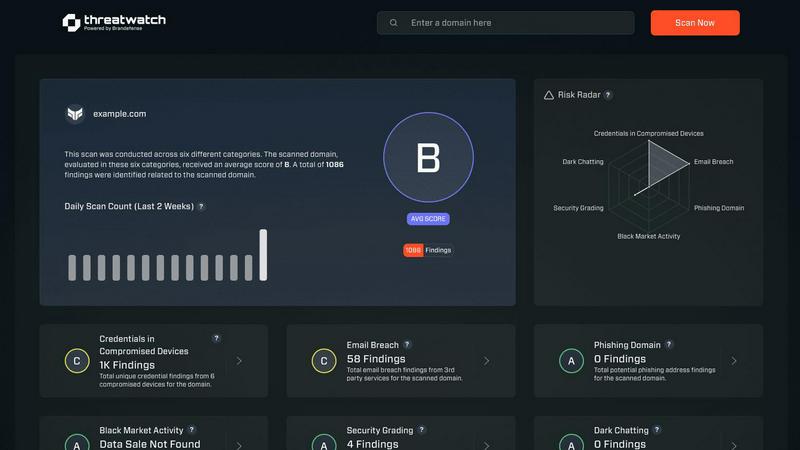
In today’s digital landscape, the threat of cyber attacks looms larger than ever. Organizations must navigate a complex web of vulnerabilities and exposures that can jeopardize their data integrity and resilience. Enter Threat Watch, a cutting-edge cybersecurity intelligence solution designed to empower businesses with the insights they need to safeguard their assets effectively. Tailored for organizations of all sizes, Threat Watch provides a comprehensive assessment of critical security categories, including compromised credentials, breached accounts, phishing addresses, and dark web contents. With real-time insights and automated assessments, users can quickly identify, prioritize, and mitigate risks. This proactive approach not only enhances cyber health but also fosters a culture of security awareness, enabling teams to respond to threats swiftly and efficiently. Discover the power of Threat Watch and transform your approach to cybersecurity.
You may also like:
finban
finban empowers you to confidently plan cash flow for hiring, taxes, and investments without the chaos of Excel.
Zignt
Zignt simplifies contract management with automated templates, secure signing, and real-time collaboration for teams.
aVenture
Navigate the startup landscape with AI-powered intelligence to discover and track emerging companies.